EMAIL THREAT PROTECTION
ADVANCED PROTECTION
EMAIL THREAT PROTECTION
Protect the entire Office 365 environment from advanced threats such as business email compromise and credential phishing. Investigate and remediate attacks automatically.
Supports organizations throughout the lifecycle of an attack.
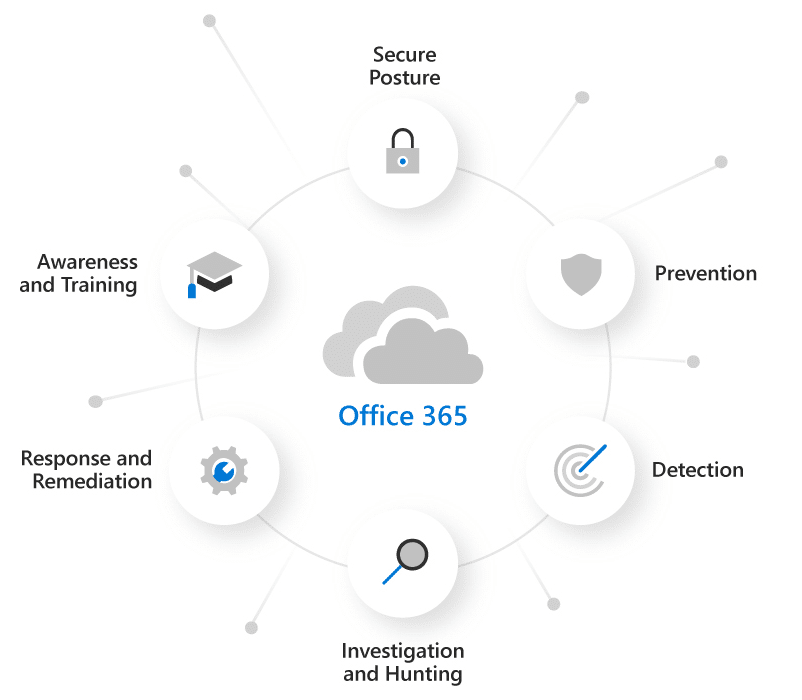
Prevention & Detection
The simplest way to stay secure is to prevent attacks from occuring in the first place.
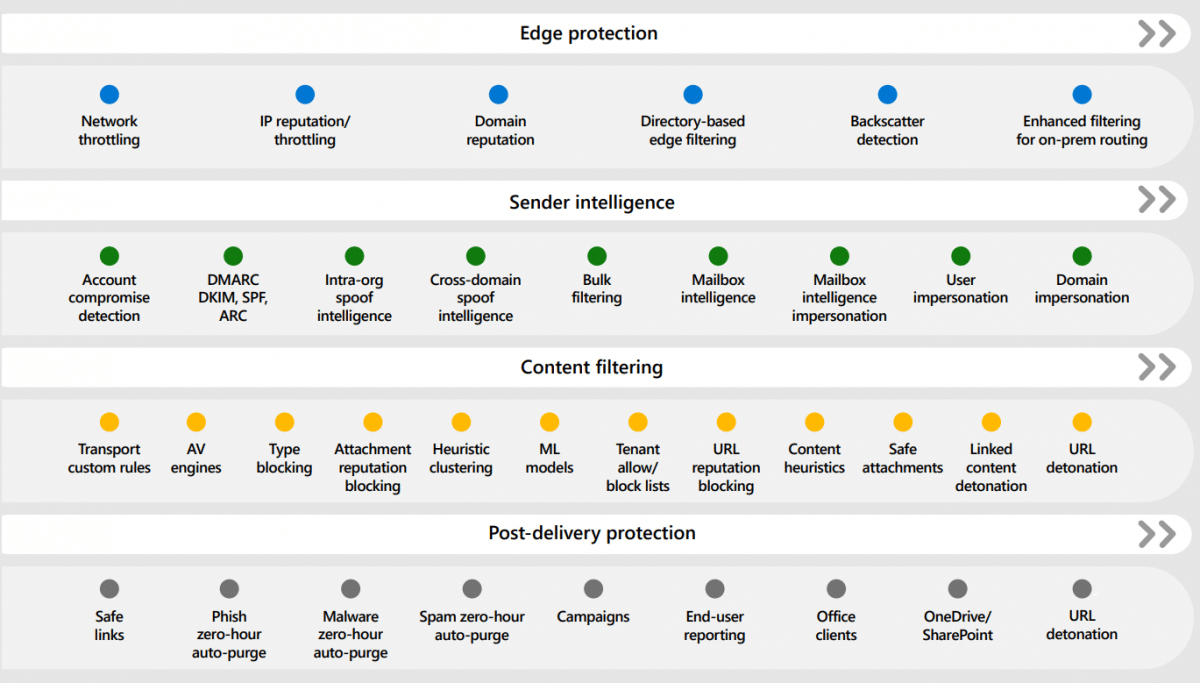
Office 365 employs industry-leading artificial intelligence to detect malicious and suspicious content and correlate attack patterns to identify campaigns specifically designed to evade detection. Our powerful filtering stack protects against a wide range of volume-based and targeted attacks, such as business email compromise, credential phishing, ransomware, and advanced malware.
Where the email is coming from by understanding the source
- Around 25% of all malicious messages received are immediately blocked at the edge before being delivered to an inbox.
- Simultaneously, machine learning models on the edge determine email traffic patterns for your domain and, if necessary, block anomalous email traffic.
What is inside the email that could be compromising
- To detect malicious content, we use a combination of standard anti-virus and anti-malware engines, as well as our Safe Attachment and Safe Links capabilities.
- Attachments or links in emails are opened in a sandbox environment, where the content is analysed by our machine learning models, which look for malicious signals and perform deep link inspection, allowing zero-day malicious attachments and links to be detected.
Who the sender is and if the person, brand, and domain are authentic
- To prevent spoofing or Business Email Compromise attacks, we authenticate the source to ensure that the sender is who they claim to be.
- SInternal emails are subjected to the same security measures as external emails.
- Emails sent between domains owned by your organisation are validated by our anti-spoof technology to ensure they truly originated in your organisation.
- In the case of external domains, our spoof intelligence checks to see if the domain has been configured in accordance with SPF, DKIM, and DMAC standards. If not, it will observe and learn message sending patterns from the domain to detect spoofed messages.
- To protect your high-profile users from impersonation, mailbox intelligence employs a machine learning model to create a contact graph of who they are normally in contact with, deciphering anomalous and good behaviour to detect impersonation attempts of trusted individuals. What is the content of the email in your organisation?
HOW IT WORKS
GET AN IT SOLUTIONS QUOTE
We’ll chat about your business, how you use technology, and what you want to get out of IT.
Lets Talk

We’ll chat about your business, how you use technology, and what you want to get out of IT.
Choose Your Plan

If we’re the right fit, you’ll choose the IT service agreement that works best for your organization.
Start Your Experience

Within days, you’ll be experiencing IT like never before.
Schedule a meeting with Stefan
or call +64 09 930 6930
SCHEDULE A MEETING WITH ONE OF OUR Local CONSULTANTS
Schedule a meeting with Steve
or call +64 09 930 6930






